Cybersecurity is a complex and ever-changing field that affects every aspect of your business. You may find yourself wondering about some common scenarios that could indicate a potential threat or vulnerability. Here are the big 4 threats to be on a lookout for:
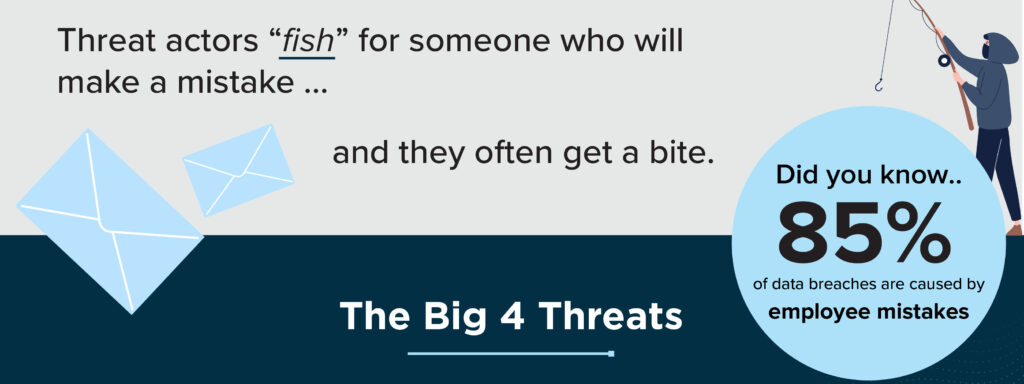
Malware:
This is any malicious software that can harm your computer or network, such as viruses, worms, trojans, spyware, adware, etc. Malware can infect your devices through various means, such as phishing emails, malicious downloads, removable media, etc. Malware can steal your data, damage your files, monitor your activities, display unwanted ads, etc.
End Goal: To harm, extort, or scare
Ransomware:
This is when hackers encrypt your files or lock your computer and demand a ransom to restore access. The ransom may be in the form of money, cryptocurrency, or other valuable data. If you don’t pay, you may lose your data permanently or face other consequences.
End Goal: To Harm, extort, or scare
Phishing:
This is when hackers send fraudulent emails or messages that appear to come from legitimate sources, such as your bank, your supplier, or your colleague. The goal is to trick you into clicking on a malicious link, opening an infected attachment, or providing sensitive information, such as your password, credit card number, or personal details.
End Goal: To exploit information for financial gain
Data Breach:
This is an unauthorized access or disclosure of sensitive or confidential information that can compromise the security and privacy of individuals or organizations. Data breaches can occur due to various reasons, such as cyberattacks, human errors, system failures, or malicious insiders. Data breaches can have serious consequences, such as identity theft, financial losses, reputational damage, legal liabilities, or regulatory penalties.
End Goal: To exploit information for financial gain, enjoy cognition, damage reputation
We understand technology can be overwhelming.
Check-up on your cyber health with a complimentary risk assessment today. A&B IT Solutions specializes in cybersecurity technology and can help your business stay protected.
